Call us toll-free at 877-449-0458
or email us at Sales@CorporateArmor.com

Key
Features
Inside
the MX
MX Series
Overview

Introducing the Meraki MX84 Security Appliance
Comprehensive Security in a Single Box, from the Premier Cisco Meraki Partner, Corporate Armor.
by clicking the image above or
contact one of their Security
Focused Sales Engineers
at 877-449-0458.
Meraki is introducing a powerful security appliance for the branch. Say hello to the new MX84 security appliance. The MX84 packs a real punch, with double the performance and capacity of its predecessor. Port counts are up on the new model, with two dedicated WAN ports for active-active Ethernet/VPN WAN links. LAN connections have increased too, with 8 Ethernet ports (up from 4 on the previous model) and the addition of 2 brand new SFP fiber ports.
Since the MX84 (and the other MX models) support dual WAN connections, it’s important to ensure that both connections can be used to their fullest potential. To that end, Meraki is announcing support for dual-active VPN connectivity and Intelligent WAN (IWAN) features. With Meraki IWAN, customers will be able to configure their security appliances to support automatic policy-based and performance-based routing decisions, ensuring more demanding applications get the bandwidth they require, and seamless failover in the event a VPN connection is dropped for any reason.
Every Meraki device - including wirelesss access points, Ethernet switches, and security appliances - connects over the Internet to Meraki’s datacenters, which run Meraki’s cloud management plat- form. These connections, secured via SSL, utilize a patented protocol that provides real time visibility and control, yet uses minimal band- width overhead (typically 1 kbps or less.)
Product Highlights
• 500 Mbps Stateful Firewall Throughput
• Supports up to approximately 200 users
• VPN throughput: 120 Mbps
• 3G / 4G failover via USB modem
• Interoperates with standards-based IPsec VPNs
• Google SafeSearch and YouTube for Schools
• Lifetime hardware warranty with advanced
replacement included
• 10 × GbE (2 WAN), 2 × SFP, and 1 × USB 2.0
interface (for 3G/4G failover)
• Identity-based policies
• Auto VPN™ self-configuring site-to-site VPN
• Client VPN (IPsec)
• User and device quarantine
• VLAN support and DHCP services

MX Cloud-Managed
Security Appliances
Call us toll-free at 877-449-0458
or email us at Sales@CorporateArmor.com

Key
Features
The
Technology
Cloud-based
Management
Cisco Meraki MX Security Appliances are ideal for organizations with large
numbers of distributed sites. Since the MX is 100% cloud managed, installation
and remote management are simple. The MX has a comprehensive suite of of
network services, eliminating the need for multiple appliances. Services include
a next-generation firewall content filtering web search filtering SNORT® based
intrusion prevention, web caching, WAN optimization, multiple WAN uplinks
and 4G failover.
UTM Capabilities
• Identity-based security policies and application management.
• Content filtering: CIPA-compliant content filter, safe-seach
enforcement (Google/Bing), and YouTube for schools.
• Intrusion Prevention: PCI Compliant IPS using industry-leading
SNORT® signature database from SourceFire.
• Application-aware traffic control: set bandwidth policies based
on Layer & application type (e.g. YouTube, Skype, P2P).
Feature-Rich Unified
Threat Management
Branch Gateway Services
• Built-in DHCP, NAT, QoS, and VLAN management services.
• Web caching: accelerates frequently accessed content.
• Link bonding combines multiple WAN links into a single
high-speed interface with policies for QoS, traffic shaping,
and failover.
• Layer 3 failover: automatic detection of layer 2 and layer 3
outages and fast failover, including 3G/4G USB modems.
• WAN optimization: data redundancy elimination, protocol
optimization and compression provide bandwidth savings
up to 99%.
Industry-Leading Cloud Management
• Unified WAN, LAN, and wireless LAN management through a
web-based dashboard.
• Template based settings scale from small deployments to large,
multi-site deployments with tens of thousands of devices.
• Role-based administration, email alerts on configuration change,
connectivity issues and power loss, and auditable change logs.
• Summary reports with user, device, and application usage
details archived in the cloud.

Site-to-Site VPN with 4G Failover
• Auto VPN: automatic routing table generation, IKE/IPsec setup and
key exchange via Cisco Meraki's secure cloud.
• Automatic failover to secondary WAN link or 4G connection.
• Interoperates with standards-based IPSec VPNs.
• Automated MPLS to VPN failover.
• Client VPN: L2TP IPSec support for native Windows, Mac OS X, iPad
and Android clients with no per-user licensing fees.
Back
to Top

Call us toll-free at 877-449-0458
or email us at Sales@CorporateArmor.com

Key
Features
The
Technology
Cloud-based
Management
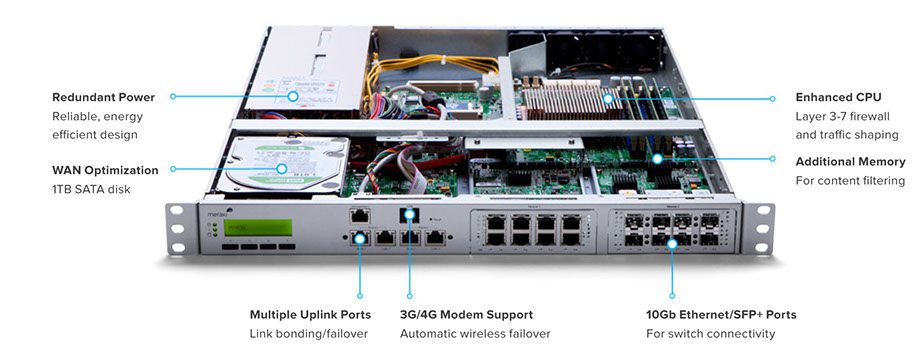
Inside the Cisco Meraki MX
Ironclad Security for Edge Networks
The MX hardware platform is purpose-built for Layer 7 deep packet inspection, with advanced security features including IPS, content filtering web search filtering anti-virus/anti-phishing, and IPsec VPN connectivity, while providing the throughput and capacity for modern bandwidth-intensive networks.
Layer 7 fingerprinting technology lets administrators identify unwanted content and applications and prevent recreational apps like BitTorrent from wasting precious bandwidth.
The integrated Sourcefir SNORT® engine delivers superior intrusion prevention coverage, a key requirement for PCI 2.0 compliance. The MX also uses the Webroot® BrightCloud URL categorization database for CIPA / IWF compliant content-filtering and Kaspersky® SafeStream engine for anti-virus / anti-phishing filtering.
Best of all, these industry-leading Layer 7 security engines and signatures are always kept up-to-date via the cloud, simplifying network security management and providing peace-of-mind to IT administrators.
Meraki’s founders invented Cloud Networking while working as grad students at M.I.T. Cisco Meraki now has a complete line of cloud networking products that power over 20,000 customer networks, including massive global deployments with tens of thousands of devices.
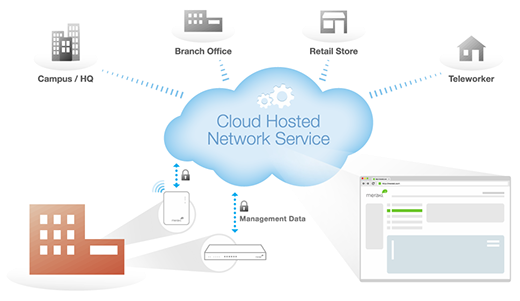
Cloud Managed Architecture
Built on Cisco Meraki’s award-winning
cloud-managed architecture, the MX
is the only 100% cloud-managed
Unified Threat Management appliance.
MX appliances self-provision,
automatically pulling policies and
configuration settings from the cloud.
Powerful remote tools provide network-
wide visibility and control, and enable
administration without on-site
networking expertise.
Cloud services deliver seamless firmware
and security signature updates, automatically establish site-
to-site VPN tunnels, and provide 24x7 network monitoring.
Moreover, the MX’s browser-based management dashboard
completely eliminates the need for training.
What is Cloud Networking?
Cloud Networking provides centralized management, visibility, and
control without the cost and complexity of controller appliances or
overlay management software. Cisco Meraki products are built from
the ground up for cloud management, and come out of the box with
centralized management, layer 7 device and application visibility, real
time web-based diagnostics, monitoring, reporting, and much, much
more. Cisco Meraki deploys quickly and easily, without training or
proprietary command line interfaces.
MX400 shown, features vary by model

Call us toll-free at 877-449-0458
or email us at Sales@CorporateArmor.com

Key
Features
The
Technology
Cloud-based
Management
The Meraki security solution includes a complete,
robust feature set right out of the box. No additional
purchase required.
Identity-Based Firewall
Automatically assigns firewall and traffic shaping
rules, VLAN tags, and bandwidth limits to enforce
the right policies for each class of users.
Identity-Based Firewall
Automatically assigns firewall and traffic shaping
rules, VLAN tags, and bandwidth limits to enforce
the right policies for each class of users.
Identity-Based Firewall
Automatically assigns firewall and traffic shaping
rules, VLAN tags, and bandwidth limits to enforce
the right policies for each class of users.
Identity-Based Firewall
Automatically assigns firewall and traffic shaping
rules, VLAN tags, and bandwidth limits to enforce
the right policies for each class of users.
Identity-Based Firewall
Automatically assigns firewall and traffic shaping
rules, VLAN tags, and bandwidth limits to enforce
the right policies for each class of users.
Identity-Based Firewall
Automatically assigns firewall and traffic shaping
rules, VLAN tags, and bandwidth limits to enforce
the right policies for each class of users.
Identity-Based Firewall
Automatically assigns firewall and traffic shaping
rules, VLAN tags, and bandwidth limits to enforce
the right policies for each class of users.
Identity-Based Firewall
Automatically assigns firewall and traffic shaping
rules, VLAN tags, and bandwidth limits to enforce
the right policies for each class of users.
Intuitive, Centralized Management
Remotely deploy Cisco Meraki Security Appliances in minutes through zero-touch cloud provisioning. Synchronize security settings across thousands of sites using templates. Securely connect branch locations in 3 clicks in Meraki’s intuitive, web-based dashboard.
The Meraki dashboard provides deep visibility and control over all of your Security Appliances from any Internet-accessible device, anytime, anywhere. View networked clients, bandwidth consumption, and application usage across all sites - and push policies to block, shape, or whitelist activity to optimize performance and user experience.
Try an MX for yourself and discover
the power of cloud networking.

©Copyright 2015 - Corporate Armor Inc. - All Rights Reserved - All Logos, Trademarks, Descriptions, Documents & Images are the property of their respective owner.